Sophos UTM v9 comes with the tcpdump utility, which lets you run packet captures from the shell. This is great and all, but in order to look at those pcaps with Wireshark, you need to pipe to a file, copy the file, then run Wireshark against it.
- Sophos Utm Tcpdump Wireshark
- Sophos Utm Tcpdump Interface
- Sophos Utm Tcpdump To File
- Sophos Utm Cli Tcpdump
- Sophos Firewall Tcpdump
Sophos UTM v9 comes with the tcpdump utility, which lets you run packet captures from the shell. This is great and all, but in order to look at those pcaps with Wireshark, you need to pipe to a file, copy the file, then run Wireshark against it. Annoying. All of it.
What if we could remotely capture packets over an SSH tunnel? YES… turns out it's a bit tricky if you're on Windows, and the authentication piece to get root access without having to do the loginuser first. How? Keep reading…
First, the necessary ingredients:
- Sophos UTM
- Wireshark (or your favorite pcap application)
- Putty suite (specifically Plink and PuttyGen)
- SG UTM 3,738 ideas Sophos Central 2,960 ideas Sophos Mobile 536 ideas.
- Sophos UTM (SG), like almost all Linux based systems, has the native functionality to perform a tcpdump to capture and show network packet information. This information is very useful in troubleshooting connectivity issues as they show every packet that the firewall has to handle.
- Shell to the back-end of the appliance On both LAN1 and LAN2 interfaces run the following command: tcpdump -i port 67 or port 68 -e -n -vv You should see the 4 steps of DHCP communication. If the Discover leaves the LAN1 interface and you do not see the DHCP server send an offer then the issue is on the DHCP server.
- Using nucleotide Sophos utm tcpdump VPN can't help if you unwisely upload ransomware or if you area unit tricked into disposition up your data to a phishing attack. Finding the best rid of VPN is an exercise in balancing those restrictions. TunnelBear, for example, lets you demand whatsoever server on its network but limits you to 500MB-1GB per.
To start, we'll need to enable Shell Access, with public key authentication, and with Root access but only with SSH key.
We need to use PuttyGen to generate the key pair we'll use for root authentication, so open it, Generate the key, then copy the Public Key into the Authorized Keys for root in the UTM, apply and save… and also Save private key to somewhere you'll remember. We'll need this for Plink.
There's our new key…
Then run the actual magic using Plink. Take the following command as an example:
Sophos Utm Tcpdump Wireshark
plink -ssh root@firewall.domain.com -i C:ssh-priv.ppk 'tcpdump -s 0 -U -n -w – not port 22 and not host 192.168.0.1' | 'C:Program FilesWiresharkWireshark.exe' -k -i –
Replace the SSH connection string for your actual firewall FQDN, the filename of ssh-priv.ppk for the location of your saved Private Key generated with PuttyGen, and the not host 192.168.0.1 with the IP address of the firewall from the interface you're reaching it.
Wireshark will open and start showing packets. You can smile and jump now.
You can modify the tcpdump parameters to better match the capture, for example, using -i eth1 to capture a specific interface, or filter specific traffic… once you're done, just close Wireshark and CTRL+C the command.
Note, if you're doing this capture remotely over WAN or Internet, it will tunnel ALL packets over SSH, so it will take up a lot of bandwidth…
Have fun!!!
Quick Overview |
Problem
If the primary ADSL connection fails, the failover succeeds to the standby interface with no
issues, what doesn't work as intended is falling back to the primary connection when it is back up…
It can be argued that the monitoring for the primary connection is not setup as intended which is not the
case… I actually configured the UTM to monitor the default gateway for the WAN connection (the first hop in the traceroute
of the primary ADSL connection ISP) because if i monitor the router itself or any public IP it's going to be up anyways
regardless of the WAN connection being used.
Why A Backup Wan Connection Is Always Needed
The main issue does not lie in losing internet connection, there are other things to consider like being able to connect remotely to a machine in the network when the primary connection goes down to see what's wrong and to be able to connect to wireless security cameras…
Prerequisites
-A router flashed with open source firmware likeDD-WRT or
any linux device in the network with bash shell.
Sophos Utm Tcpdump Interface
-A 4G modem with an ethernet interface or any backup WAN connection preferably of course, from a
different ISP.
-Of course, a Sophos UTM with Uplink Balancing & Uplink Monitoring configured, either running
on a VM or on a dedicated device.
Current Configuration
The VM has three virtual interfaces configured in bridged mode, this way they are seen by |
I have a Sophos UTM running on an Oracle VirtualBox virtual machine on an Intel NUC, the NUC has
only one ethernet interface and a wireless interface but i am only using the ethernet interface and in the VM configuration, i
have created three virtual interfaces in bridged mode:
-LAN interface.
-Primary WAN interface set to use the main router as default gateway.
-Backup WAN interface set to use the 4G modem as default gateway, in my case i am using the
TP-Link MR-3020 as default gateway.
-In case you will be using the TP-LINK MR-3020 or a similar device then you will also need a 4G
USB modem plugged in to the USB interface of the MR-3020.
Creating the interfaces in bridged mode allows them to appear to other devices in the network as
physical interfaces, no device in the network can tell the difference.
Problematic setup – Uplink Balancing is set to |
The issue arises when the UTM tries to ping the aforementioned first hopvia the
backup wan interface which will never work because they are totally different ISP's, simply.
To Confirm The Root Cause Of The Problem
To confirm the root cause of the problem, we will initiate a failover by disabling the primary WAN
connection on the router and then monitoring the monitoring traffic 🙂
Disconnecting the WAN from the DD-WRT router's interface and simulating a |
But first, we have to setup our tcpdump on the UTM and note the behaviour of the normal monitoring
traffic, we will use tcpdump flag -e to show the MAC addresses of the interfaces:
elutm:/root # tcpdump -nei eth1 host 10.45.3.134 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth1, link-type EN10MB (Ethernet), capture size 65535 bytes 08:22:14.847351 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:22:14.869246 e0:3f:49:9c:5a:78 > 08:00:27:a1:c4:f6, ethertype IPv4 (0x0800), 08:22:29.849211 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:22:29.870805 e0:3f:49:9c:5a:78 > 08:00:27:a1:c4:f6, ethertype IPv4 (0x0800), 08:22:44.852065 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:22:44.873276 e0:3f:49:9c:5a:78 > 08:00:27:a1:c4:f6, ethertype IPv4 (0x0800), |
The ICMP's are working as expected, to the correct IP and to the router's MAC
address
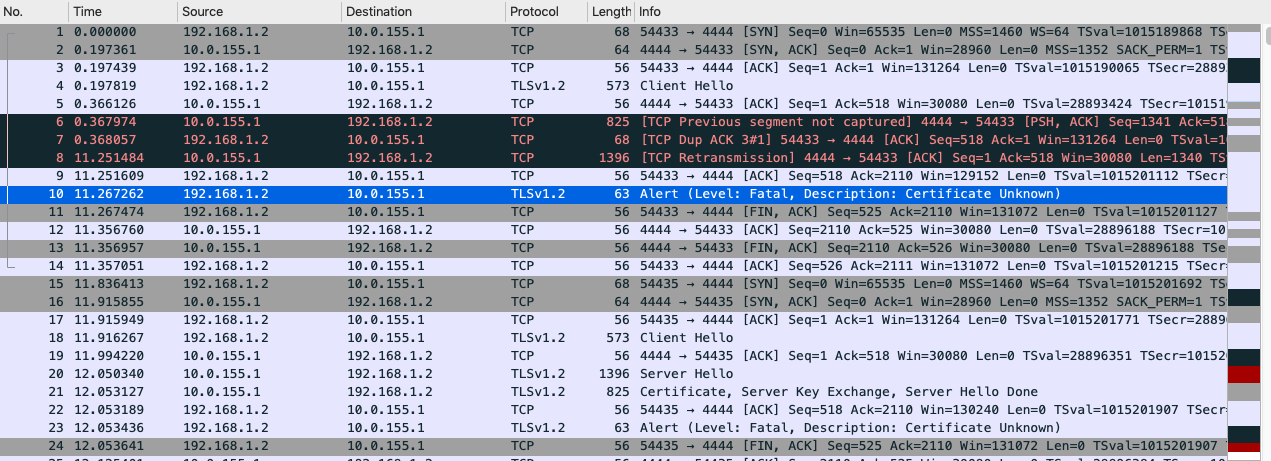
Now let's disable and re-enable the WAN connection and capture the monitoring traffic on
both WAN interfaces eth1 and eth2
elutm:/root # tcpdump -nei eth1 host 10.45.3.134 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth1, link-type EN10MB (Ethernet), capture size 65535 bytes 08:39:00.768403 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:39:01.021330 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:39:01.272891 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:39:01.524324 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), |
elutm:/root # tcpdump -nei eth1 host 10.45.3.134 P1780 ford. tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth1, link-type EN10MB (Ethernet), capture size 65535 bytes 08:46:00.924674 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:46:01.175700 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:46:01.427553 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:46:01.678668 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), |
As per the captures above, although the primary WAN connection is back up, for some reason the UTM
cannot reach it on both interfaces and therefore no fallback to the primary WAN interface…
How To Fix The WAN Failover Issue
To fix this, i came up with the idea to have the UTM monitor an IP inside the LAN instead of
monitoring the default gateway of the ISP, but we also need the reachability of that IP to be dependent on the reachability of
the default gateway of the ISP…
The solution is very simple… A small bash script on the router (or any linux based OS with
CLI) will ping the default gateway of the primary ADSL ISP every 30 seconds, if it succeeds it will add an additional IP on the
router's LAN interface, this IP address will be used for the Sophos' UTM monitoring instead of the gateway of the
ISP, so here's how it will work.
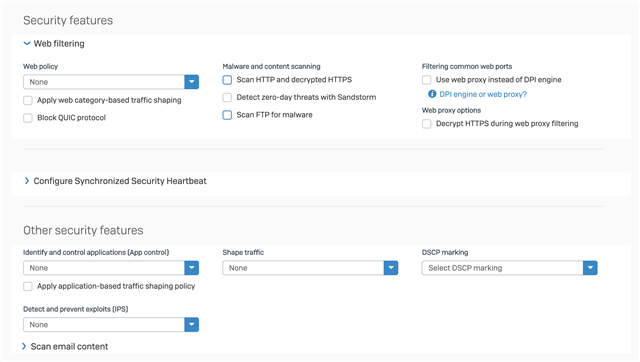
-On router boot, assume WAN connection is up and add an additional IP address to the
router's LAN interface.
-The Sophos UTM will test the reachability of the internal IP 192.168.1.250.
-Every 30 seconds, the router will ping the default gateway of the ISP.
-If the default gateway of the ISP is not reachable, change the additional IP address on the
router's LAN interface to any other IP address.
-If at anytime 192.168.1.250 is unreachable, UTM will failover to the backup WAN
connection.
-A while TRUE loop continues to ping the default gateway of the ISP.
-If we are on the backup WAN connection, since the IP being tested for is an internal IP address
so the UTM can reach it regardless of which WAN connection is active.
-If the router can ping the default gateway of the ISP, it will re-add the previously deleted
additional IP on the router's LAN interface 192.168.1.250.
-The UTM will detect that the monitored host is up and will fall back to the primary WAN
connection :).
Under 'Interfaces > Uplink Balancing', this is how it looks like with the |
The Bash Script In Action
One of the most powerful features of DD-WRT is the ability to add custom scripts that are executed at startup
that can do virtually anything, i have added this script to the 'Custom scripts' section underAdministration > Commands and called it via the 'Startup script'
section.
#!/bin/sh
|
Sophos Utm Tcpdump To File
The Final Result

Now let's disable and re-enable the WAN connection and capture the monitoring traffic on
both WAN interfaces eth1 and eth2
elutm:/root # tcpdump -nei eth1 host 10.45.3.134 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth1, link-type EN10MB (Ethernet), capture size 65535 bytes 08:39:00.768403 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:39:01.021330 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:39:01.272891 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:39:01.524324 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), |
elutm:/root # tcpdump -nei eth1 host 10.45.3.134 P1780 ford. tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth1, link-type EN10MB (Ethernet), capture size 65535 bytes 08:46:00.924674 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:46:01.175700 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:46:01.427553 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), 08:46:01.678668 08:00:27:a1:c4:f6 > e0:3f:49:9c:5a:78, ethertype IPv4 (0x0800), |
As per the captures above, although the primary WAN connection is back up, for some reason the UTM
cannot reach it on both interfaces and therefore no fallback to the primary WAN interface…
How To Fix The WAN Failover Issue
To fix this, i came up with the idea to have the UTM monitor an IP inside the LAN instead of
monitoring the default gateway of the ISP, but we also need the reachability of that IP to be dependent on the reachability of
the default gateway of the ISP…
The solution is very simple… A small bash script on the router (or any linux based OS with
CLI) will ping the default gateway of the primary ADSL ISP every 30 seconds, if it succeeds it will add an additional IP on the
router's LAN interface, this IP address will be used for the Sophos' UTM monitoring instead of the gateway of the
ISP, so here's how it will work.
-On router boot, assume WAN connection is up and add an additional IP address to the
router's LAN interface.
-The Sophos UTM will test the reachability of the internal IP 192.168.1.250.
-Every 30 seconds, the router will ping the default gateway of the ISP.
-If the default gateway of the ISP is not reachable, change the additional IP address on the
router's LAN interface to any other IP address.
-If at anytime 192.168.1.250 is unreachable, UTM will failover to the backup WAN
connection.
-A while TRUE loop continues to ping the default gateway of the ISP.
-If we are on the backup WAN connection, since the IP being tested for is an internal IP address
so the UTM can reach it regardless of which WAN connection is active.
-If the router can ping the default gateway of the ISP, it will re-add the previously deleted
additional IP on the router's LAN interface 192.168.1.250.
-The UTM will detect that the monitored host is up and will fall back to the primary WAN
connection :).
Under 'Interfaces > Uplink Balancing', this is how it looks like with the |
The Bash Script In Action
One of the most powerful features of DD-WRT is the ability to add custom scripts that are executed at startup
that can do virtually anything, i have added this script to the 'Custom scripts' section underAdministration > Commands and called it via the 'Startup script'
section.
#!/bin/sh
|
Sophos Utm Tcpdump To File
The Final Result
Sophos Utm Cli Tcpdump
Now the UTM sees the primary interface as up and the interface connected to the 4G modem as
standby, which is exactly the intended behaviour.
Sophos Firewall Tcpdump
The ADSL connection is up and the 4G connection is standby in case of any issues with |